Yesterday, there were two BGP routing incidents in which several high-profile sites (Google, Apple, Facebook, Microsoft, Twitch, NTT Communications and Riot Games) were rerouted to a previously unused Russian AS. The incidents only lasted about three minutes each, but demonstrated once again the lack of routing controls like those called for in MANRS that could have prevented this from happening.
As reported in BGPmon’s blog post on 12 December 12,
“…our systems detected a suspicious event where many prefixes for high profile destinations were being announced by an unused Russian Autonomous System.
Starting at 04:43 (UTC) 80 prefixes normally announced by organizations such Google, Apple, Facebook, Microsoft, Twitch, NTT Communications and Riot Games were now detected in the global BGP routing tables with an Origin AS of 39523 (DV-LINK-AS), out of Russia.”
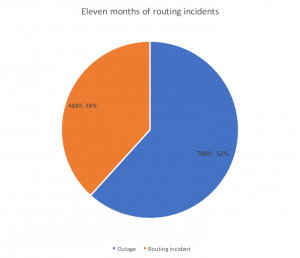
Either a configuration mistake or a malicious attack, it propagated quickly through the Internet without visible obstacles. This was one of almost 5000 route leaks and hijacks in 11 months of 2017. For comparison, network outages during the same period caused almost 8000 incidents (source: https://bgpstream.com/):
In practice, the efficacy of corrective actions strongly depends on the reliability and completeness of information related to expected routing announcements. And these qualities quickly deteriorate with every routing hop on the path. Meaning that the easiest and most effective way to prevent such incidents from a customer is by its direct transit provider. In the case of AS39523 – that is AS31133 (Megafon).The Internet is an interconnected system and its security is only as strong as its weakest link – the least secure network operator. But the concept of “defense in depth” is more applicable here: If a network emits a false routing announcement, there should be many chances to correct it.
Deploying the simple, low-cost, low-risk measures promoted by MANRS is vitally important for all network operators. Had Megafon implemented Action 1 “Prevent propagation of incorrect routing information,” the false announcements yesterday would have been stopped at the first hop. Had reliable data been available about what prefixes DV-LINK-AS is authorised to advertise, others could have prevented that too.
Is your network doing all it can to prevent incidents like this? Read the MANRS document, follow the Implementation Guide, and Join MANRS!

