 With it’s 1.0 release last week, the Jitsi soft phone became the first VoIP client I know of to support DNSSEC. Jitsi, formerly known as the “SIP Communicator”, is available for Windows, Mac OS X or Linux from:
With it’s 1.0 release last week, the Jitsi soft phone became the first VoIP client I know of to support DNSSEC. Jitsi, formerly known as the “SIP Communicator”, is available for Windows, Mac OS X or Linux from:
Jitsi has a great range of features including support for voice and video calls, chat/IM, desktop sharing, conference calls, wideband audio and much more. It works with the SIP (Session Initiation Protocol) and XMPP (Jabber) protocols and connects to common services like GoogleTalk, AIM, Yahoo!Messenger, Facebook chat, etc. It’s also free and the source code is all available.
Jitsi has supported SIP and XMPP over IPv6 for quite some time now, but with this new release adds support of DNSSEC courtesy, I learned, of some funding from the NLnet Foundation and the University of Applied Sciences and Arts Northwestern Switzerland (FHNW). The DNSSEC code itself was implemented by Ingo Bauersachs from this university.
Essentially what Jitsi now does if you enable DNSSEC is to validate the signing of the SRV records in DNS that provide the address information for the remote end of the SIP or XMPP connection.
To step back and explain a bit further, if Alice wants to call Bob (to be cliche), and she knows his SIP address is “sip:bob@example.com”, her SIP client, IP-PBX or other SIP server (depending upon configuration) is going to perform a DNS lookup on “example.com” to retrieve the relevant SRV records. These records will provide the IP address(es) of the SIP server on Bob’s side. Alice’s SIP software will then connect to those IP addresses to send the appropriate SIP INVITE to start a conversation with Bob.
But how does Alice’s software know that the SRV records retrieved from DNS are correct? How can it know that they were not tampered with?
What if she is trying to call her bank and an attacker is redirecting her to another SIP server where there is a similar call center or IVR? (Okay, leaving aside the fact that at this moment you may not be able to make SIP connections to many banks… but that is changing slowly.)
Enter DNSSEC.
If the “example.com” domain is signed via DNSSEC, including all the SRV records, then the VoIP client can validate that the SRV records are in fact correct and the connection can be made knowing that it is to the intended recipient based on the SIP address.
From a configuration point of view, there has been one more screen added to Jitsi’s preferences:
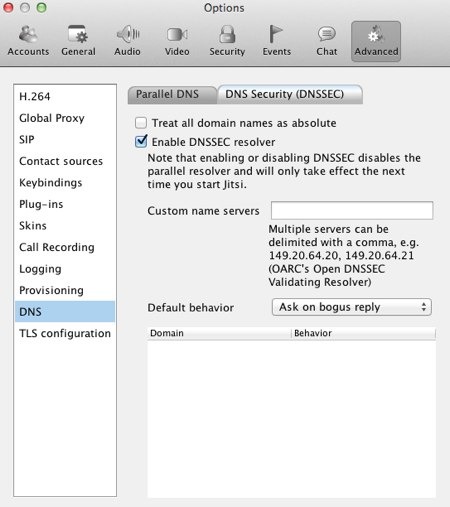
At this moment there is no documentation on the Jitsi site about the DNSSEC features (they are working on it… and open to any offers of assistance! ;-), but I asked Ingo Bauersachs about the configuration of the resolver. His reply was this:
Libunbound, the library Jitsi is using, is validating the DNSSEC chain, but it’s not a full resolver. Queries for DNSKEY, DS, etc. are sent to the OS’s resolver, or if configured, to the “Custom name servers”.
The option to override the OS’s default resolver is there because during development, the only servers supporting all relevant record types were from DNS-OARC and Verisign.
The choice not to use libunbound as a fully recursive resolver was performance and that it’s for one simply not the job of an application to perform recursive DNS queries.
In my own case, I’m running a local instance of DNSSEC-Trigger and that is my operating systems default resolver. I’ll be able to perform the DNSSEC resolution without any issues. Ingo also indicated that the table at the bottom of the Preferences panel will fill up with domains as you start to connect to sites (any sites – DNSSEC-signed or not). You can then specify what the DNSSEC-related behavior is for individual domains.
That’s how this all works, of course, when you have both publicly accessible SIP servers with SRV records – and DNSSEC signatures on those records. There may not be a whole lot of those sites out there quite yet, but having apps like Jitsi available will only help.
If you have a SIP- or XMPP-based VoIP or IM system (or “Unified Communications” system to use the appropriate marketing buzzwords) where you can sign your domain with DNSSEC, definitely check out Jitsi and see how it works. And as you have it working, I’d certainly love to hear from you and perhaps feature some examples in future blog posts.
The Jitsi team is also very interested in feedback and indicated that sending messages to the “dev” mailing list (and joining that list if you want) would be the best way to proceed.
I’m also personally interested in trying this out in a test environment… if you’ve got a SIP server with a domain that is DNSSEC-signed, please drop me a note as I’d like to try calling you. 🙂
Kudos to the NLnet Foundation for funding this work and to Ingo Bauersachs and the Jitsi team for implementing it all. I’m looking forward to seeing where this goes!
P.S. Wikipedia has a decent page on SRV records if you want to know more about these record types.
