On Sunday, 25 February, the first day of APRICOT 2018, a “Routing Security BoF” (birds of a feather: An informal discussion group) was organized to address the ever-growing routing related incidents happening on daily basis. We have discussed routing security in general within the Asia Pacific region but there was a need to have a platform for open and candid discussion among the network operator community to find a possible way forward, where operators can share their approach in securing their own infrastructure and keeping the internet routing table clean as well.
A quick introduction was provided by the moderator (Aftab Siddiqui) on why it is important to have this BoF. Here are the introductory slides.
The first technical community presenter was Yoshinobu Matsuzaki (Maz) from Internet Initiative Japan (IIJ), the first ISP in Japan started in 1992. IIJ is one of the few ISPs in the region implementing prefix filtering, source address validation for their end customers, and making sure that all their routing information is reflecting the current status in the peeringdb for AS2497. IIJ was the first Asia Pacific ISP to join MANRS (Mutually Agreed Norms for Routing Security), a global initiative, supported by the Internet Society, to work with operators, enterprises, and policymakers to implement crucial fixes needed to eliminate the most common routing threats. See the slides.
The rest of the BoF was based on a panel discussion, with panelists representing some of the top global CDNs (Content Delivery Networks) along with the technical lead of the MANRS initiative from the Internet Society.
- Kam Sze Yeung – Akamai
- Marijana Novakovic – LinkedIn
- Jonny Martin – Lime Light Networks
- Andrei Robachevsky – Internet Society
The discussion started with the following questions:
Q1. You just heard from one of the largest ISP in the region (IIJ) and, being one of the biggest CDN providers globally, what measures do you take to ensure that you are keeping the internet routing table clean?
A1 (summary). CDNs mostly rely on the peering fabrics and they do put filters in place to safeguard their infrastructure and also don’t usually pollute the global routing table. They can’t control any peer network and hence cannot avoid any accidental/intentional prefix hijack. To safeguard against such incidents, all CDNs actively monitor the global routing table to quickly fix incidents and reduce the outage or impact.
Q2. There are ISPs that implement routing security and there those who don’t. Do you have the same peering policies for both? Do you enforce any policy to make sure that your peering partners are doing the right things?
A2 (summary). It is not possible for CDNs to create different peering policies on the basis of network reputation, but they do make sure that they have good visibility of the network in order to find the problem as early as possible. Also, it is hard for CDNs to de-peer in case of an incident because there are commercial interests in place as well. The counter argument from Andrei (ISOC) was: CDNs can’t apply different policies to networks/peers on the basis of reputation because it is realistically difficult to differentiate the bad from the majority of good peers. This is where MANRS can provide a platform to show if a network is accidentally/intentionally polluting the internet routing table.
Q3. Do you see any benefit of RPKI and BGPSEC to secure internet routing in the future?
A3 (summary). It was clear from the discussion that BGPSEC is too new to have any constructive discussion; there are many changes required in the protocol and even after that it is optional for a peer to use BGPSEC. However, RPKI can play some role in the future but at the moment no CDN is actively pursuing RPKI as a solution. The topic of RPKI resulted in some interesting debate between Geoff Huston and panelists.
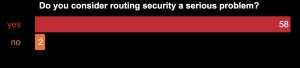
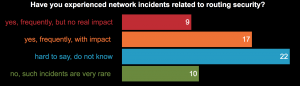
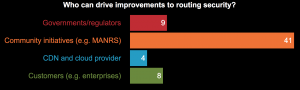
At the end of the panel discussion we asked four questions through an interactive poll and the results were very interesting and encouraging.
Around 62 members of the community participated in this poll, which clearly shows that the vast majority of them consider routing security a problem we need to address. While some are not clear if there was an impact on internet services because of routing security incidents (lack of data), it was very clear that networks don’t follow guidelines to implement routing security because there is no incentive for them to do so. At the end the clear winner was MANRS, as most respondents believe that only a community-driven initiative such as MANRS can convince the network operators to implement routing security. (Here’s how to join MANRS.)