How can use DNSSEC if you register your domain name with one registrar, but actually host the DNS records on the name servers of another DNS hosting provider? Or if you host the DNS records on your own name server?
As we were putting together our list of DNS registrars and hosting providers supporting DNSSEC, we thought we should provide a step-by-step example of how you could do exactly this – use DNSSEC with a different registrar and DNS hosting provider.
For the example, we chose two of the registrars/hosting providers we’ve written about: GKG.net and Dyn, Inc.. We could certainly have used other registrars but given that the DNS hosting package we’d already purchased at Dyn, Inc, included management of up to 10 domains, it seemed to make sense to use them. Plus, both companies support both DNSSEC and IPv6.
The Internet Society Deploy360 Programme does not recommend or endorse any particular domain registrars. The information provided here is to assist users of this registrar to understand how to sign their domains with DNSSEC and is part of a larger program of gathering this information across all domain registrars known to support DNSSEC. If you know of an additional registrar we should include, please contact us.
In this example, we decided to use the domain “dnssec-test-gkg.com” we’d already registered with GKG.net and host its DNS records over at Dyn, Inc. The steps involved were:
1. Set up the DNS zone and records at the DNS hosting provider. Each DNS hosting provider has its own web interface and system for adding records. In this case, we just created a brand new zone at Dyn, Inc., and added an A and AAAA record to the zone mostly just to have a few more records in the zone.
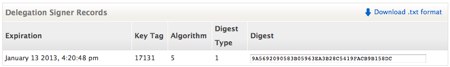
2. Still at the DNS hosting provider, sign the domain with DNSSEC. We just followed the steps we outlined for signing domains with DNSSEC using Dyn, Inc. The end result is that we have a signed domain with a DS record:
3. At the registrar, change the name server records for the domain to point to the name servers of the DNS hosting provider. Again, each registrar has a slightly different web interface. Here was how GKG.net let us change the name servers:
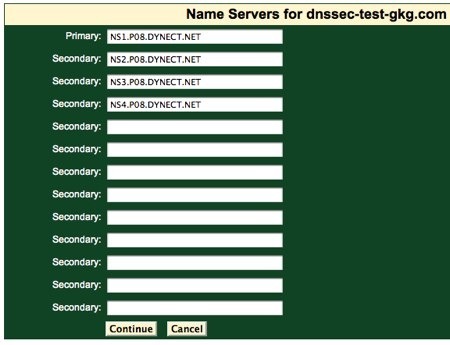
This change may take some period of time to propagate through the larger DNS infrastructure. Until the change has fully propagated, people may still see DNS records coming from the old name servers.
At this point we have a domain signed with DNSSEC at the DNS hosting provider and we’ve changed the records at the registrar to point to the name servers of the DNS hosting provider.
We’re almost ready to go.
If we run the test domain through the DNSSEC Analyzer tool, we’ll see that there is still a problem:
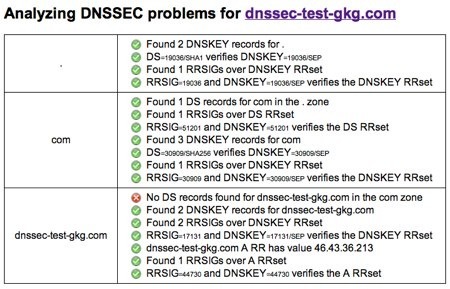
The issue is that we have not yet set up a Delegation Signer (DS) record at the registrar that ties our DNSSEC signed zone into the global chain of trust. We need to add this bit of “glue” between the DNSSEC-signed top-level domain and our actual DNSSEC-signed zone records.
4. To finish the linkage, at the registrar, add a DS record, copying the information provided to you from the DNS hosting provider. GKG.net provides an easy web interface for this:
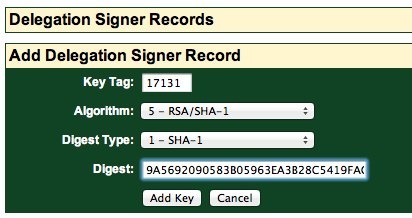
Pressing the “Add Key” should then add the DS record. In our case, perhaps because of the timing while creating this tutorial, we received a warning that GKG.net could not verify that the DS record was correct:
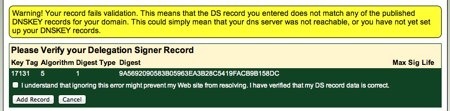
After double-checking back at the DNS hosting provider that all the information was correct, we checked the box indicating that we had verified the record was correct and pressed the Add Record button. The result was a DS record:
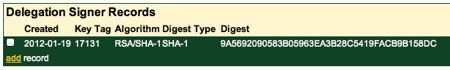
GKG.net automatically published our DS record and there was nothing more for us to do.
5. Finally, verify that DNSSEC works using a tool such as Verisign Labs’ DNSSEC Analyzer. Here are the results for our test domain:
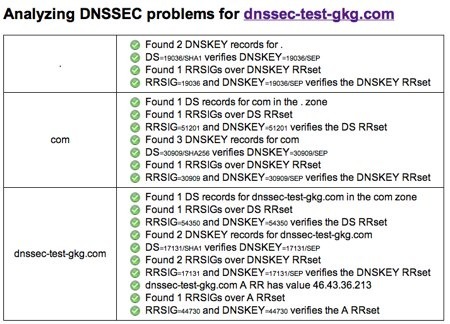
Note that there may be some propagation delays and so you may have to wait a bit after adding the DS record to see the linkage reflected in the DNSSEC Analyzer results. In our case, the wait was only a few minutes but it may be different for you.
With that, we now have DNSSEC working with a domain registered with one registrar (GKG.net) and hosted at a different provider (Dyn, Inc.). The steps are going to be basically the same for any registrar and hosting provider, although the actual user interfaces may be wildly different. Note, too, that instead of using a DNS hosting provider you could be operating your own name server and doing all the DNSSEC signing on your own system.
Regardless of whether you use a DNS hosting provider or use your own name server, the critical point is that BOTH your domain registrar and your DNS hosting provider must support DNSSEC. (See our list.)