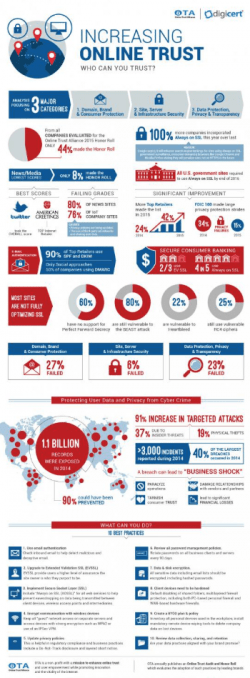
The 2015 Online Trust Audit includes a composite analysis focusing on three major categories; a company’s data protection, security and privacy practices, including over two-dozen criteria. The 2016 Presidential Candidates and IRS eFile service provider audits are based on the 2015 methodology along with 2016 enhancements in SSL scoring and privacy requirements including disclosure of honoring status of browser based Do-Not-Track settings. Read more from the OTA blog.
Sites were eligible to receive 300 total base points, including up to 100 points in each category and up to 30 bonus points. The audit evaluated over 900 websites across multiple sectors including; the Internet Retailer Top 500, the FDIC Top 100 Banks, the Top 50 Federal Government sites, the Top 50 Social Networking sites, the Top 50 News/ Media sites, and OTA Members. New to the 2015 Audit will be an examination of the top 50 Internet of Things (IoT), vendors focusing on the “home automation” and “wearables” (health and fitness) solution categories. (Each sector evaluated on same criteria including OTA Members.) Organizations who qualify for the 2015 Honor Roll, can apply to license the program logo. More >
Each sector was scored in three categories:
- Domain, Brand & Consumer Protection
- Site, Server & Infrastructure Security
- Data Protection, Privacy & Transparency
The 2015 scoring has been expanded and enhanced with additional weight and granularity to key practices. To qualify for the Honor Roll sites had to receive composite score of 80% or better and a score of at least 55 in each of the three categories.
Data sampling of survey sites, their DNS, server infrastructure, email and privacy policies is planned to be completed between April 20 and May 15, 2015. In total, it is estimated more than 500 million email headers and approximately 100,000 web pages will be analyzed. It is important to note a site’s policies and practices may have changed since the sampling and the data only reflects findings based on this period of time.
Addressing the ever changing security and privacy landscape as well as regulatory requirements, criteria continues to evolve with the bar raising in all areas. This year as in years past, criteria that were previously considered bonus points are now part of baseline requirements. Examples include adoption of DMARC, increased SSL granularity, as well as upgrading from SHA1 certificates and Do Not Track (DNT) disclosures.
With the goal to drive adoption of best practices allowing all companies the ability to access their status and optimize their scores, OTA published the 2015 criteria in mid-February 2015 on the OTA website and external facing newsletters.
It should be noted that this research is based on a “slice of time” and individual companies may have since adopted or changed their security and privacy practices. We also recognize that the sites examined might be using other technologies (which our tools or research did not detect) to authenticate domains or subdomains, secure their infrastructures, track users on their sites, etc. Due to the sensitivity of this data and risk of disclosing vulnerabilities, individual organization’s scores and data are not publicly available. Information will be provided to site owners upon written request and verification. For details, including reporting fees, please send an email to admin @ otalliance.org.
COMPONENTS OF THE COMPOSITE SCORES
DOMAIN, BRAND & CONSUMER PROTECTION
- Email Authentication (SPF & DKIM) – The report analyzed more than 500 million emails and the respective DNS infrastructure of leading sites and subdomains. Email authentication assesses efforts to protect users from domain and email spoofing via the adoption of two industry leading protocols, Sender Policy Framework (SPF) and Domain-Keys Identified Mail (DKIM). Sites received maximum scores by implementing both SPF and DKIM authentication at the top level domain (i.e. yourdomain.com) as well as on their respective delegated subdomains (i.e. email.youremail.com). Verification of DKIM-signed email required review of the email headers of individual emails via sampling providing by Agari, Microsoft and Return Path. Augmenting previous year’s methodology, OTA subscribed to marketing email newsletters and / or submitted inquiries to sites, to review responses providing for increased granularity of email data. Results were integrated into the composite scoring and factored as a component of the baseline points required to qualify for the Honor Roll. Verification of SPF records was completed using the OTA DNS record lookup tool.
- Updated – Domain-based Message Authentication, Reporting & Conformance (DMARC) – DMARC standardizes how email receivers perform email authentication using the SPF and DKIM mechanisms. Sites that have published DMARC records receive a positive score. This year publishing a “reject” or “quarantine” policy is part of the baseline scoring for email authentication. Due to growing adoption and success, additional weighting was given to sites publishing a DMARC record this year. DMARC Information >. Verification was completed using the OTA query tool.
- Domain Locking – Domain locking is a security enhancement offered by most registrars to help prevent unauthorized transfers of your domain to another registrar or web host by locking your domain name servers. When your domain is locked, you’ll be substantially protected from unauthorized third parties who might try to redirect your name servers or transfer your domain without your permission. Sites receive negative points if their domain is not locked.
- New – Transport Layered Security (TLS) for Email – New for 2015, sites which have implemented “opportunistic TLS” will receive bonus points. TLS helps prevent eavesdropping on email as it is carried between email servers that have enabled TLS protections for email. Just as TLS can be used to secure web communications (HTTPS), it can secure email transport. To maximize the content security and privacy, TLS is required between all the servers that handle the message including hops between internal and external servers.
- Domain Name System Security Extension (DNSSEC) – Testing for DNSSEC was completed by Verisign and IDD which queried the DNSSEC records. Sites adopting DNSSEC receive bonus points.
- New – Bonus points for Bot and Botnet Protection – Sites will be checked for basic protection against web scraping, vulnerability scanning, scripted form completion, and other common bot-driven activities.
SITE, SERVER & INFRASTRUCTURE SECURITY
- Updated – Server and SSL Configuration – Sites were evaluated using a combination of data and tools from DigiCert, GlobalSign, High-Tech Bridge SA, Qualys Labs, RiskIQ, RiskIQ, SiteLock and Symantec. These tools provide visibility into the server architecture, configuration and digital certificate. In addition sites were evaluated for iFrame exploits, XSS scripting as well as for the presence of malware or malicious links. Testing evaluated for weak keys, protocols, algorithms, and server misconfigurations that can enable attackers to exploit system vulnerabilities and compromise SSL communications. SSL Labs tool increased security requirements and added new grading options in January 2015. More > Refinements to the SSL scoring include applying negative scoring is the following are observed:
- Servers that use SHA1 certificates.
- Sites vulnerable to POODLE
- Servers that don’t support TLS_FALLBACK_SCSV
- SSL 3 is supported
- If RC4 is supported
- If the chain is incomplete
- Fail servers that have SSL3 as their best protocol
- New – Bonus point for use of Organization Validation (OV) and EV-SSL certificates; neutral scoring for Domain Validated (DV) and self-signed receive a negative score). Organization Validation (OV) or Extended Validation (EV) practices contain the verified name of the entity that controls the website. Certification authorities (CA) issuing these certificates check with third parties to establish the official name of the organization and where they are located. In contrast, Domain-Validated certificates are typically verified through automated processes. A DV certificate contains no identifying information in the organization name field. Typically, this value just re-states the domain name or simply says “Persona Not Validated.” Although the certificate supports transaction encryption, the end-user cannot trust the certificate to confirm who is on the other end.
- Extended Validation SSL Certificates (EV SSL) – EV SSL offers trust mechanisms visibly confirming the identity of the site to the user. The 2015 analysis focused on all sites with SSL connections, not limiting the evaluation to consumer facing e-commerce or banking sites. Cybercriminal target business-to-business, social networking and government sector sites with non-EV Certificates. Acquiring an Extended Validation certificate requires extensive verification by the certificate authority. Sites that have implemented EV SSL Certificates received additional bonus points.
- Always On SSL (AOSSL) – Sites were evaluated for the adoption of AOSSL and /or HTTP Strict Transport Security (HTTP) as best practices to secure sensitive data between a user’s device and a web site. With the advent of widely available tools, criminals can “sidejack” cookies and data packets from unsuspecting users. Sitejacking allows hackers to intercept cookies (typically used to retain user-specific information such as username, password and session data) when they are transmitted without the protection of SSL encryption. Sites supporting AOSSL receive additional points, with added weight from previous years. This capability was measured using the Qualys SSL Server Test and other tools to look for Strict Transport Security and verified by auditors accessing the sites.
DATA PROTECTION, PRIVACY & TRANSPARENCY
- Privacy Policy & Tracking Score – Using third-party data from AVG Technologies, TRUSTe and additional OTA criteria, sites were analyzed for their privacy policy and data collection practices. A Privacyscore evaluates privacy risk based on a website’s published policies about protection of personal data and the privacy qualifications of third-parties seen to be collecting data on the site. Website privacy policies regarding sharing, deletion, retention policies, disclosure notices and vendor confidentiality were reviewed by analysts. Scoring for third-party tracking companies (reflecting policies on anonymity, boundaries, choice, retention and oversight) were weighted based on their prevalence in site scans. Sites were crawled for a period of over 96 hours to observe data collection and onsite tracking. It is important to note scores are dynamic and can change based on the mix of third-party tracking and revisions to privacy policies. Results were integrated into the composite scoring and factored as a component of the baseline points required to qualify for the Honor Roll.
- Updated – Notice If Data Is requested & Shared Based on Court Orders – Addressing the increased legal disclosures being made by third parties and governments, site were evaluated for disclosure polices. Recommended copy to maximize scoring includes “To the extent we are legally permitted to do so, we will take reasonable steps to notify you in the event that we are required to provide your personal information to third parties as part of legal process.”
- Updated – Do Not Track Browser Settings (DNT) – In response to the State of California disclosure requirement for a site regarding Do Not Track, Websites privacy policies were evaluated for compliance as part of the core scoring. In addition sites which publicly disclose they are honoring the browser-based DNT setting received bonus points. Such an assertion would be in addition to any such notice a user is presented when visiting a site and does not preempt any such notice. A DNT signal asserts a user’s request to not collect and share their online data. Sites that Honor the DNT signal will receive additional bonus points. For an example of a DNT notification best practice review the OTA Privacy Policy. For additional information see the updated California Guidelines
- Public vs. Private WHOIS registration – Sites that are registered by proxy or private registration received a negative score, reflecting a lack of transparency. While it is recognized that sites may choose to opt-in for private domain name registration, public facing sites are discouraged from doing so and consumers should exercise caution when interacting with sites that have made their domain information private. Results were integrated into the composite scoring as a negative score for sites with private registrations and factored as a component of the baseline points required to qualify for the Honor Roll.
- Tag Management System or Privacy Solution – Sites that implement a tag management system or a standalone privacy solution receive bonus points. A tag management system provides a site operator visibility of data collection practices and how to proactively manage third party activities. A standalone privacy solution monitors third party activity site for the site operator. They enhance the ability to manage analytics tools, marketing tags, and other tag-based technologies that may collect and share data. Websites were scanned using tools from Ensighten and InfoTrust LLC.
- Data Breach & Loss Incidents – Companies who have experienced a data breach or a data loss incident since January 1, 2014 received negative points. See 2015 OTA Data Protection & Breach Readiness Guide
- FTC / FCC / State Settlements – Companies which have been in violation of the FTC Act including settlements and judgments since January 1, 2014 receive negative points. The FTC Act and related FCC regulation focuses on consumer protection, including but not limited to deceptive advertising, privacy and data security practices.
- Layered Short Notices – Site receive bonus points for adoption a short layered notice. Plan for 2016 include moving short / layered notices to part of the core scoring. See OTA’s Privacy Policy as an example.
- New – Privacy Policies with icons. Building on short layered notices, site with the use of consumer friendly icon receive additional bonus points. See examples Publishers Clearing House and TRUSTe.
SECTORS EVALUATED
- Internet Retailer Top 100 (IR100) & Internet Retailer Top 500). Ranking based on revenue as reported by Internet Retailer Magazine, produced by Vertical Web Media. Ranking as of April 7, 2015. http://www.internetretailer.com/top500/.
- FDIC top 100 banks (FDIC 100). Based on net assets as reported by the Federal Deposit Insured Corporation. Ranking as of December, 31, 2014. http://www.managingmoney.com/fdic.php.
- Top 50 Federal Government sites (Fed 50). Based on a combination of consumer traffic and recent cybercriminal targeting of Federal Government sites including forged email campaigns and phishing sites. Includes Cabinet level agencies at risk of such exploits.
- Top 50 Social Networking and sharing sites (Social 50). Includes social networking, dating entertainment, gaming, document storage, photo and colloboration sites..
- Top 50 News and Media sites (News 50). Includes top ranked news, content and media sites, (non-ecommerce or social).
- OTA Member Companies (OTA Members). Includes commercial members including consumer and business to business sites. Does not include academia, law enforcement, professional members, public sector, non-profits or members companies who joined since May 1, 2015. https://otalliance.org/about-us/members.
ACKNOWLEDGEMENTS
Data and analysis has been provided in part by: Agari, AVG Technologies, Distill Networks, Disconnect, DigiCert, Ensighten, GlobalSign, High-Tech Bridge SA, IID, InfoTrust LLC, Microsoft, Qualys, Return Path, SiteLock, SSL Labs, Symantec, ThreatWave, VeriSign and TRUSTe.