Email security, authentication, and related best practices are the foundation of the Internet Society’s Online Trust Alliance work to promote the integrity of email and standards to counter email fraud and phishing. OTA publishes a set of recommendations that prescribe the adoption of freely available and standards-based email authentication technologies as an effective response to rampant abuse of the email channel.
Three email authentication standards form one of the major components of the annual Online Trust Audit:
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM)
- Domain-based Message Authentication, Reporting & Conformance (DMARC)
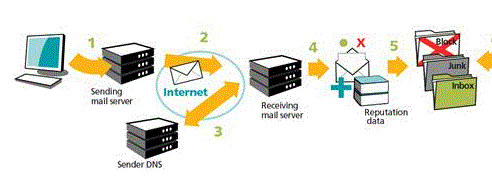
The Figure below outlines how email authentication provides the ability for ISPs and receiving networks to detect and block spoofed and forged email. (See related overview and recommendation of TLS for email to help protect the privacy of email in transit).
Best Practices
OTA recognizes the critical role email plays in today’s online ecosystem, and publishes the following recommendations:
- Implement both SPF and DKIM for top-level domains, “parked” domains (not used for email) and any major subdomains seen on websites or used for email.
- Optimize SPF records with no more than 10 DNS lookups.
- Implement DMARC, initially in “monitor” mode to get receiver feedback and verify accuracy of email authentication, and eventually move to “enforcement” (signal a “reject” or “quarantine” policy to receivers).
- Mandate the use of DMARC reporting capabilities with RUA (aggregate) and RUF (message-specific forensic) reports.
- Implement inbound email authentication checks and DMARC on all networks to help protect against malicious email and spear phishing purporting to come from legitimate senders.
- Implement opportunistic TLS to protect email in transit between mail servers.
- Ensure that domains are locked to prevent domain takeovers.
- Implement DNSSEC to help protect a site’s DNS infrastructure.
- Deploy IPv6.
- Implement Distributed Denial of Service (DDoS) mitigation technologies and processes.
- Implement multi-factor authentication.