DDoS
Internet of Things Devices as a DDoS Vector
As adoption of Internet of Things devices increases, so does the number of insecure IoT devices on the network....

ISOC Rough Guide to IETF 99: Internet Infrastructure Resilience
IETF 99 is next week in Prague, and I’d like to take a moment to discuss some of the...

Holiday DDoS Attacks: Targeting Gamers (Plus Five Things You Can Do)
Over the past few years, a new tradition has emerged, the Holiday DDoS Attack. While distributed denial of service...
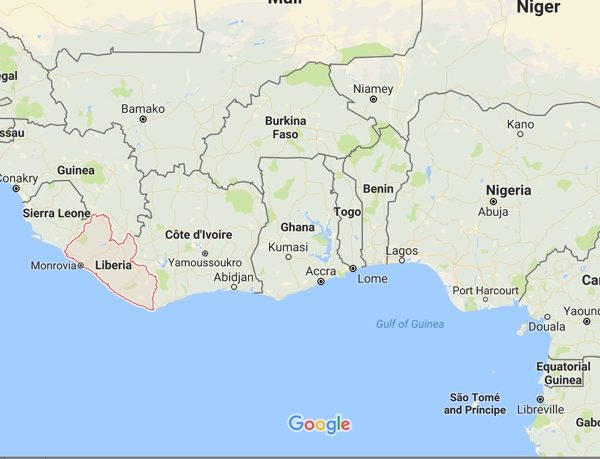
The DDoS Attack Against Liberia – we must take collective action for the future of the Open Internet
If it was not clear yet: the Internet Society condemns those that perform large-scale distributed denial-of-service (DDoS) attacks on...

How To Survive A DNS DDoS Attack – Consider using multiple DNS providers
How can your company continue to make its website and Internet services available during a massive distributed denial-of-service (DDoS)...
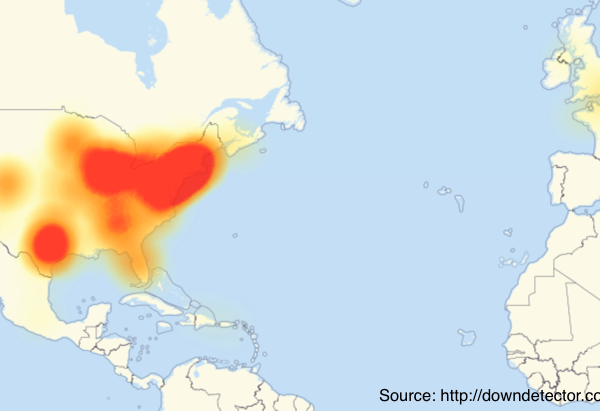
Trust isn’t easy: Drawing an agenda from Friday’s DDoS Attack and the Internet of Things
Last week, millions of infected devices directed Internet traffic to DNS service provider Dyn, resulting in a Distributed Denial...

New Whitepaper Explores Ways to Make IP Spoofing a Problem of the Past
In March 2013, Spamhaus was hit by a significant DDoS attack that made its services unavailable. The attack traffic reportedly peaked...

Coordinating Attack Response at Internet Scale
How do we help coordinate responses to attacks against Internet infrastructure and users? Internet technology has to scale or...